Dale Myers posted a blog entry a few days ago about a problem he’d found in 1Password: while passwords in AgileBits’ vaults were secure, metadata was stored in the clear. And this was intentional, allowing web-based access to the vault to retrieve information without requiring the 1Password app.

Learn how to synchronize Dropbox with '1password'. Don't forget to check out our site for more free how-to videos! Dropbox makes it easy to password protect PDFs and other files without the need for third-party software. Before you share a link to a PDF, Word Doc, or other file or folder in your Dropbox account, just set a password for the link so the recipient can only open it. 1Password automatically creates backups of the standalone vaults on your Mac or Windows PC every day if there have been any changes made since the last backup. This includes vaults you’re syncing with Dropbox or iCloud. If you’re syncing with Dropbox or iCloud, a copy of your data is also stored separately with Dropbox or iCloud. 1password File: 1password file is encrypted and is not easy to decrypt but it is still possible that it can be decrypted if it gets in to hands of hackers. Hashcat does support 1password file decryption. Dropbox Security: Dropbox is a well known known file hosting company but they have been compromised in past.
Myers wasn’t incorrect and he wasn’t over-sensationalizing the situation. He also provided a recommendation for a solution, one that AgileBits endorsed in its blog entry responding to his post. And he continues to use the product.
Though it’s obvious, neither Myers nor AgileBits explicitly noted one important factor, however: A sniffer has to gain access to your vault. If you posted it on a website that you set up for only you to use, perhaps someone else would find or a security breach at a hosting company might provide a way in.
But if you use Dropbox for syncing, there’s little chance for easy vacuuming up of your data. I have my 1Password vault synced to two Macs and two iOS devices using Dropbox. I have two-factor authentication enabled for Dropbox, and FileVault, Touch ID, and a passcode in use on those computers and mobiles. Someone has to either get access to my Dropbox credentials and second factor, or get access to my devices in an unlocked state to grab my file. (It’s also possible Dropbox would experience a hack that would allow files to be obtained without credentials or physical access, but that would expose vast amounts of information of all kinds, rather than being a targeted effort to obtain a 1Password vault.)
Even if someone should retrieve your entire vault, the information they could get is only useful to learn about you, rather than to break into your accounts. The passwords themselves remain protected in an extremely strong manner that requires a huge amount of computational effort and substantial time to crack.
But even losing metadata makes some people nervous, and rightly so. In the wrong hands, information about what you do—where you have accounts—could be used for identity theft or harassment.
Moving on OP
1password Dropbox Sync Not Working
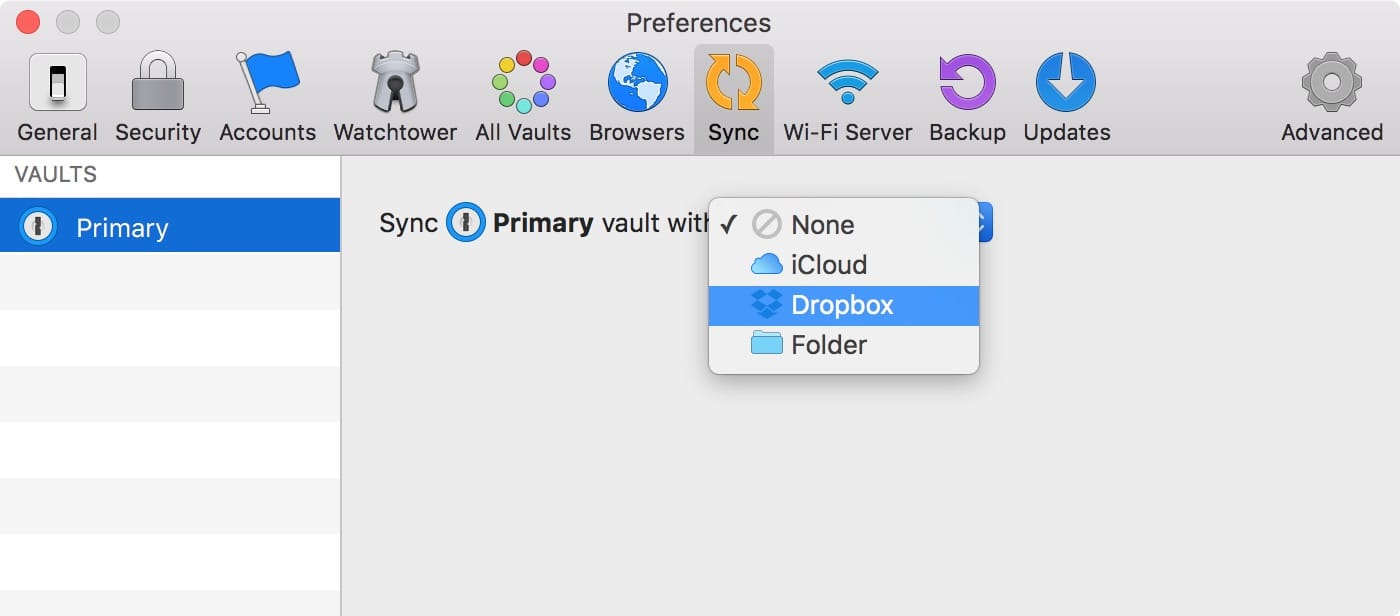
The format Myers objected to, Agile Keychain, was developed in 2008 by AgileBits as a way to allow granular updates of individual password entries without overloading the mobile device processing power that was available when the iPhone 3G was fresh and fancy. The company later developed a newer format, called OPVault, which encrypts nearly everything. Myers raised a good point by noting that Agile Keychain remains in wide use. (OPVault leaves the names of folders and categories unencrypted, as well as timestamp data, but this offers little of utility to crackers compared to URLs and user names.)
1password Not Syncing With Dropbox

As AgileBits noted in its blog entry, it didn’t migrate everyone from the old to the new, because there remained a mix of software releases and devices. Not-that-long-gone versions of 1Password—1Password 3 and older for Mac and 1Password 4 and older for iOS—can’t read OPVault, and the company didn’t want to break compatibility in the interests of security.
(OPVault is always used with iCloud, by the way. If you use iCloud, I generally recommend enabling two-step verification now and two-factor authentication as Apple rolls out its revised system more broadly in the coming months.)
You can imagine how this would have looked to customers, too. “I upgraded on my iPhone, and now my OS X version says I have to upgrade to read my passwords! What are you up to?!” Instead, they erred on the side of looking backward. AgileBits writes that they’re going to step up migration to the new format in upcoming releases across all platforms they support.
However, you can switch over today if you’re concerned about the metadata in your vault becoming accessible to anyone but yourself with just a few well-documented steps at the company’s website. Just check that all your devices have compatible versions of 1Password.
I went through them and it went off tickety-boo. I made the change in OS X, and then launched 1Password for iOS, where I went to the Sync settings and pointed the app to the new file. Because the entries were identical, just in a different format, it only took a couple of seconds for the sync process to show that it was up to date.
As capability improves and security follows, it will be more and more important that companies keep in mind and disclose to customers the decisions they made for efficiency in the past that are no longer needed. AgileBits didn’t drag its customers painfully to the new format—that’s an Apple move! Apple has no sentiment about the necessity of moving forward with no path back. But now that it’s taken stock with a prod from an outsider, we’ll all reduce our attack profile as a result.
Update: This article was updated to reflect the potential that a Dropbox breach would also allow 1Password data to be obtained, and to note that OPVault doesn’t encrypt folder and category names, nor timestamps.
