| Developer(s) | The OpenBSD Project |
|---|---|
| Repository | github.com/openssh/openssh-portable/ |
| Written in | C |
| Operating system | Unix, Unix-like, Microsoft Windows |
| Type | Command |
| License | BSD, ISC, public domain |
| Website | www.openssh.com |
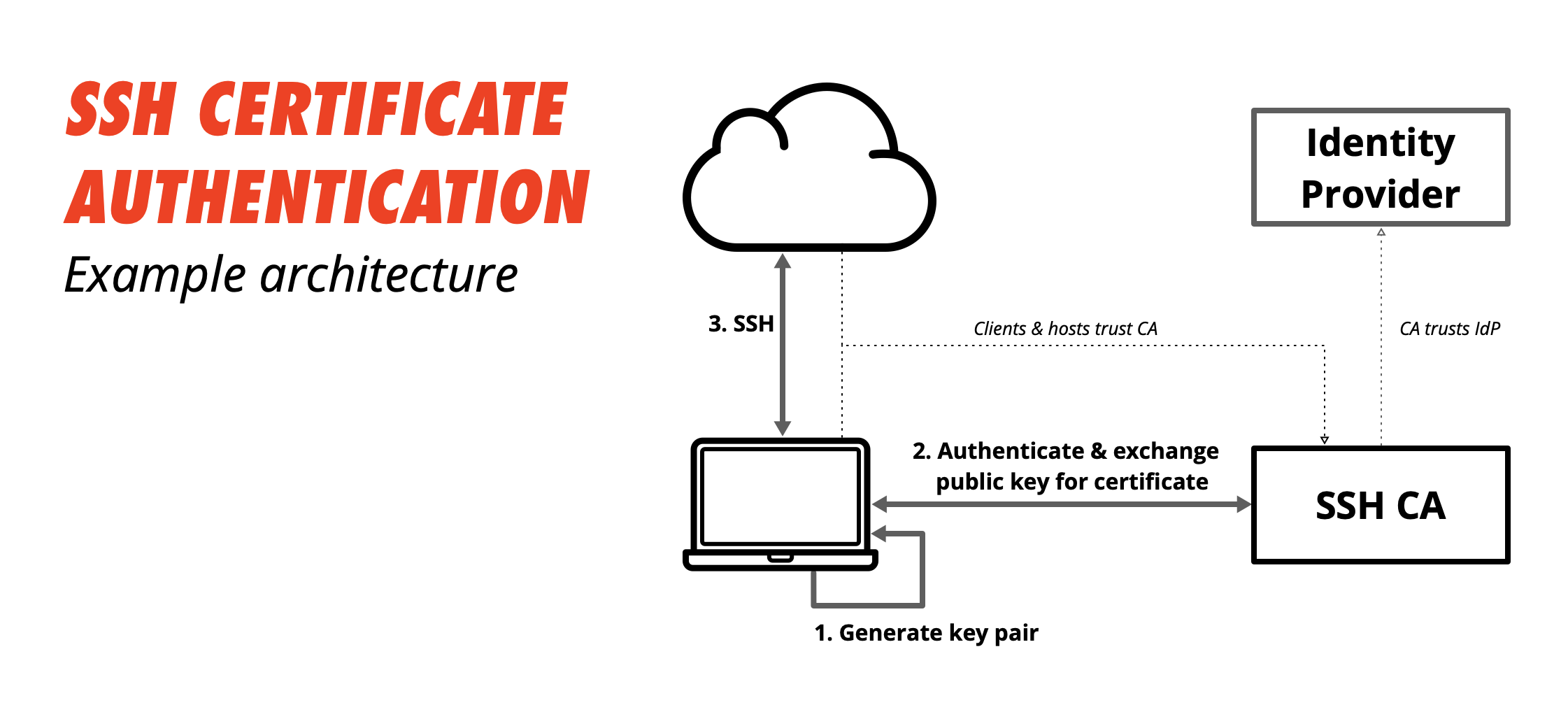
Secure Shell (SSH) is a protocol allowing secure remote login to a computer on a network using public-key cryptography. SSH client programs (such as ssh from OpenSSH) typically run for the duration of a remote login session and are configured to look for the user's private key in a file in the user's home directory (e.g., .ssh/id_rsa). For added security (for instance, against an attacker that can read any file on the local filesystem), it is common to store the private key in an encrypted form, where the encryption key is computed from a passphrase that the user has memorized. Because typing the passphrase can be tedious, many users would prefer to enter it just once per local login session. The most secure place to store the unencrypted key is in program memory, and in Unix-like operating systems, memory is normally associated with a process. A normal SSH client process cannot be used to store the unencrypted key because SSH client processes only last the duration of a remote login session. Therefore, users run a program called ssh-agent that runs beyond the duration of a local login session, stores unencrypted keys in memory, and communicates with SSH clients using a Unix domain socket. Kingdom hearts 2 final mix save file.
Security issues[edit]
ssh-agent creates a socket and then checks the connections from ssh. Everyone who is able to connect to this socket also has access to the ssh-agent. The permissions are set as in a usual Linux or Unix system. When the agent starts, it creates a new directory in /tmp with restrictive permissions. The socket is located in this directory.
There is a procedure that may prevent malware from using the ssh-agent socket. If the ssh-add -c option is set when the keys are imported into the ssh-agent, then the agent requests a confirmation from the user using the program specified by the SSH_ASKPASSenvironment variable, whenever ssh tries to connect.
After you entered your password the key is loaded in the key manager ssh-agent. You can test this by logging into the server you put your public key on. If the key is correctly loaded in the ssh agent it wont ask you for your passphrase and log you in. ('ssh -v host.with.pubkey'). Also you can have a look at your currently loaded keys by using 'ssh-add -l'. After you logged in, log out by typing 'logout'. Start SSH agent only once and add identity information without password prompt - sshaddidentity.sh. Ssh-agent creates a socket and then checks the connections from ssh. Everyone who is able to connect to this socket also has access to the ssh-agent. The permissions are set as in a usual Linux or Unix system. When the agent starts, it creates a new directory in /tmp with restrictive permissions.
On the local system, it is important that the root user is trustworthy, because the root user can, amongst other things, just read the key file directly. On the remote system, if the ssh-agent connection is forwarded, it is also important that the root user on the other end is trustworthy, because it can access the agent socket on the remote (though not the key, which stays local).
Implementations[edit]
There are many different programs that perform the same functionality as the OpenSSH ssh-agent, some with very different user interfaces. PuTTY, for example, uses a graphical user interface in its bundled Pageant ssh-agent.
There are tools designed to provide key-agent functionality for both symmetric and asymmetric keys; these usually provide ssh-agent functionality as one of their application interfaces. Examples include GNOME Keyring and KWallet.
Sims 3 male jakcet. Some monolithic SSH clients include the ability to remember SSH passphrases across sessions. Examples include: SecureCRT.
Apple macOS[edit]
On the macOS operating system, ssh-agent has been integrated since Leopard, version 10.5 in 2007. Third-party open-source implementations of ssh-agent were available previously.[1]
Microsoft Windows[edit]
OpenSSH-based client and server programs have been included in Windows 10 since version 1803. The SSH client and key agent are enabled and available by default and the SSH server is an optional Feature-on-Demand.[2][3]
References[edit]
- ^Dribin, Dave (21 August 2007). 'SSHKeychain Warning'. Dave Dribin's Blog.
- ^https://devblogs.microsoft.com/commandline/windows10v1803/
- ^https://devblogs.microsoft.com/powershell/using-the-openssh-beta-in-windows-10-fall-creators-update-and-windows-server-1709/
External links[edit]
| Wikibooks has a book on the topic of: Guide to Windows Commands |
- ssh-agent man page from OpenSSH release (part of the OpenBSD project).

Enable the SSH server in Windows
You need to add the optional feature ‘OpenSSH Server’ in Windows 10 first by going to Settings -> search for Add an optional feature -> search again for OpenSSH Client and choose to install.
Configure SSH service to automatically start
By default Windows won’t start the ssh-agent. You can tell Windows to start the service automatically in the future by running the following command in PowerShell (as Administrator).
But right now, manually start the service by running
Generate the key
Open PowerShell and follow these commands to generate SSH key on your machine. Torch web browser free download.
Keep the default location for where to save the key. This should be C:Users<username>/.ssh/id_rsa.
Generate a complex password and store in safe place, ideally a password manager.Enter this password when prompted. When complete you’ll be shown the key fingerprint and the key's randomart image.
Add key to the SSH Agent
We need to add the key to our ssh-agent so we don’t have to type the key each time we use it.
The agent will recognise that a new key is present and will ask for the passphrase.
Once entered you’ll see the confirmation message Identity added.
I still needed to manually add the key to the ssh-agent. To do so navigate to the .ssh folder where we stored our keys earlier C:Users<username>/.ssh/ and run the following with the correct key name.
This will prompt you to enter the passphrase in and once again you should see the Identity added confirmation.
Access your public key
Now we have our key we can add it to systems such as GitHub or Bitbucket. To do so follow the instructions for that particular service. We’ll need to retrieve the public key from our machine to do so.
Navigate to the .ssh folder and find the file <private-key>.pub. Open this in a text editor. The contents of this file is what you need to copy and paste into the relevant service you’re wanted to add the key to.
Testing the keys
In this example lets assume we’ve added our key to Bitbucket. We can test that the key is correctly set up by running the following command.
If all is well then we should see the logged in as message without needing to enter the passphrase
Using with Git
By now we have our key correctly stored in the SSH agent and we’re allowed to connect to the Bitbucket servers using SSH. However we might still be prompted to enter our passphrase whenever we try to perform a git command that talks to the remote.
Check Ssh Agent Log
The ssh -T command uses the Windows 10 agent so all appears to be correct, but it won’t behave the same in Git. This is due to the fact Git is using it’s own ssh agent, not the Windows 10 agent that we’ve added our keys to.
Check If Ssh Agent Is Running
We need to tell Git to use the Windows SSH agent instead of it’s own. We do this by updating the git config.
Now when we use Git, we won’t be prompted for our passphrase, even after a restart.
References
